- Home
- Popular IT Certifications
- Configuring ACLs to Filter Network Traffic
How to configure and verify ACLs to filter network traffic?
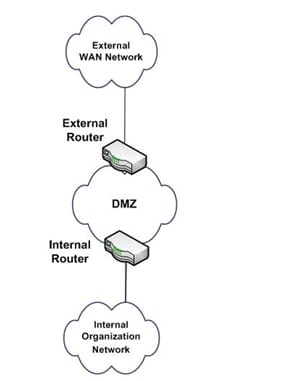
ACLs are a system filter used by switches and a few switches to allow and confine information streams into and out of system interfaces. At the point when an ACL is arranged on an interface, the system gadget examines information passing through the interface, contrasts it with the criteria depicted in the ACL, and either allows the information to stream or disallows it. There is an assortment of reasons we utilize ACLs. The essential reason is to give a fundamental level of security for the system. ACLs are not as mind boggling and inside and out of insurance as static firewalls, yet they do give security on higher velocity interfaces where line rate pace is critical and firewalls may be prohibitive. ACLs are likewise used to limit redesigns for routing from system peers and might be instrumental in characterizing stream control for system traffic. ACLs for switches are not as mind boggling or hearty as firewalls, yet they do offer a lot of firewall ability. As an IT system or security proficient, arrangement of your safeguards is discriminating to securing the system, its benefits and information. ACLs ought to be set on outer switches to filter activity against less attractive systems and known helpless protocols. A standout amongst the most well-known strategies for this situation is to setup a DMZ, or de-mobilized cradle zone in your system. This construction modeling is typically executed with two different system devices. The most outside switch gives access to all outside system associations. This switch normally has less prohibitive ACLs, however gives bigger insurance access squares to ranges of the worldwide routing tables that you wish to limit. This switch ought to additionally ensure against well-known protocols that you completely don't want to permit access into or out of your system. What's more, ACLs here ought to be arranged to confine system associate get to and could be utilized as a part of conjunction with the routing protocols to limit upgrades and the degree of courses got from or sent to system peers.
The DMZ is the place most IT experts place frameworks which need access from the outside. The most widely recognized samples of these are web servers, DNS servers, and remote access or VPN frameworks. The inside switch of a DMZ contains more prohibitive ACLs intended to secure the inner system from more characterized dangers. ACLs here are frequently arranged with unequivocal allow and deny articulations for particular locations and protocol administrations.
There are a few sorts of access control records and most are characterized for a unique reason or protocol. On Cisco switches, there are two principle sorts: standard and augmented. These two sorts are the most broadly utilized ACLs and the ones I will concentrate on in this and future articles, however there are some developed ACLs too. A percentage of the progressed ACLs incorporate reflexive ACLs and element ACLs and they are characterized as takes after. Reflexive ACLs, otherwise called IP Session ACLs, are activated from an outbound ACL for activity started from the inner system. The switch will recognize this new activity stream and make an entrance in a different ACL for the inbound way. Once the session closes, the entrance in the reflexive ACL is evacuated.
Dynamic ACLs or bolt and-key ACLs are made to permit client access to a particular source/end of the line have through a client confirmation process. Cisco executions use IOS Firewall capacities and don't ruin existing security confinements. Position and understanding of the movement stream is paramount to see in advance before you arrange an ACL on a switch interface. Understanding of the arrangement and effect of ACLs are regular inquiries in CCNA and CCNP exams and oversights in ACL position are the absolute most normal ones system overseers make amid security usage. Trust me, it befalls all of us and I am not safe to that one. Figure 2 gives a decent illustration of the activity stream concerning entrance and departure on a switch system interface.
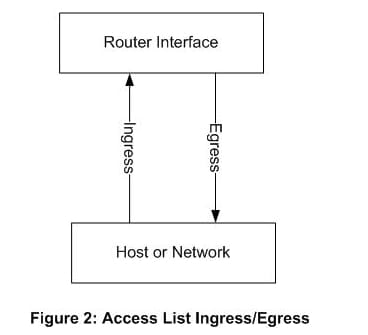
As should be obvious from this chart, entrance activity streams from the system into the interface and departure streams from the interface to the system. IT system and security experts must give careful consideration here. ACLs begin with a source address first in their design and terminus second. As you arrange an ACL on the entrance of a system interface it is essential to perceive that all nearby system or hosts ought to be seen as sources here, and the accurate inverse for the departure interface. What makes this most befuddling is the execution of ACLs on the interface of a switch that faces an outside system. Think once more at Figure 1. In that case, the entrance side is originating from the outside system and those locations are thought to be sources, while all inside system locations are ends. On the departure side, you're inside system locations are currently source addresses and the outside locations are presently destinations.as you include ports in amplified ACLs, disarray can mount. The best counsel I have before any execution is to report your streams and note your source/objective locations. We will blanket a greater amount of these executions later in ACL arrangement articles. In the 1990s the ACL and RBAC models were widely tried and used to administrate document consents. A file system ACL is an information structure (generally a table) containing passages that determine singular client or gathering rights to particular framework questions, for example, projects, procedures, or records. These entrances are known as access control sections (Aces) in the Microsoft Windows NT, Openvms, Unix-like, and Mac OS X working frameworks. Every open article contains an identifier to its ACL. The benefits or consents focus particular access rights, for example, whether a client can read from, keep in touch with, or execute an article. In a few executions, an ACE can control whether a client, or gathering of clients, may adjust the ACL on an object. Most of the UNIX and Unix-like working frameworks (e.g. Linux, BSD, or Solaris) help Posix.1e ACLs, taking into account an early POSIX draft that was relinquished. A significant number of them, for instance AIX, Freebsd, Mac OS X starting with adaptation 10.4 ("Tiger"), or Solaris with ZFS file system, help Nfsv4 ACLs, which are a piece of the Nfsv4 standard. There are two test executions of Nfsv4 ACLs for Linux: Nfsv4 ACLs help for Ext3 file system and late Rich ACLs, which brings Nfsv4 ACLs, help for Ext4 file system. On a few sorts of exclusive machine fittings (specifically switches and switches), an Access Control List alludes to decides that are connected to port numbers or IP Addresses that are accessible on a host or other layer 3, each with a rundown of hosts and/or systems allowed to utilize the administration. In spite of the fact that it is furthermore conceivable to arrange Access Control Lists focused around system space names, this is for the most part a sketchy thought on the grounds that individual TCP, UDP, and ICMP parcels don't contain area names. Hence, the gadget implementing the Access Control List should independently resolution names to numeric locations. This shows an extra assault surface for an assailant who is trying to trade off security of the framework which the Access Control List is securing. Both individual servers and also switches can have system ACLs. Access control records can for the most part be arranged to control both inbound and outbound activity, and in this connection they are like firewalls. Like Firewalls, ACLs are liable to security regulations and principles, for example, PCI DSS. The principle option to the ACL model is the Role-based access control (RBAC) model. An "insignificant RBAC Model", RBACM, could be contrasted and an ACL system, ACLG, where just gatherings are allowed as entrances in the ACL. Barkley (1997) demonstrated that RBACM and ACLG are equal. In present day SQL executions, ACL additionally oversee gatherings and legacy in a progressive system of gatherings. So "advanced ACLs" can express all that RBAC express, and are strikingly compelling (contrasted with "old ACLs") in their capability to express get to control strategy as far as the path in which directors view associations.
Working of ACL:
Switch demonstrations as a bundle channel when it advances or denies parcels as per sifting standards. As a Layer 3 gadget, a bundle separating switch uses tenets to figure out if to allow or deny activity focused around source and terminus IP locations, source port and goal port, and the protocol of the parcel. These tenets are characterized utilizing access control records or ACLs. To improve how ACL or a switch utilizes parcel separating work, envision a gatekeeper positioned at a bolted entryway. The monitor's direction is to permit just individuals whose names show up on a mission rundown to pass through the entryway. The gatekeeper is separating individuals focused around the state of having their names on the approved list. When a bundle touches base at the switch, the switch extricates certain data from the parcel header and settles on choices as indicated by the channel leads with reference to whether the bundle can pass through or be dropped. Parcel sifting procedure lives up to expectations at the Network layer of the Open Systems Interconnection (OSI) model, or the Internet layer of TCP/IP.
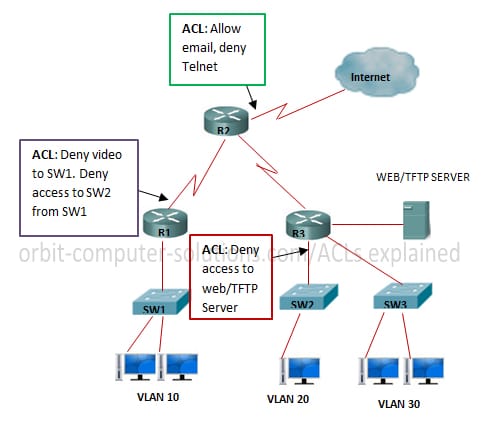
You can utilize channels on Aps to perform these undertakings:
- Confine access to the remote LAN (WLAN) system
- Give an extra layer of remote security
- You can utilize diverse sorts of channels to channel movement focused around:
- Particular protocols
- Macintosh location of the customer gadget
- IP location of the customer gadget
You can likewise empower channels to confine activity from clients on the wired LAN. IP location and MAC location channels permit or forbid the sending of unicast and multicast parcels that are sent to or from particular IP or MAC addresses. Protocol based channels give a more granular approach to confine access to particular protocols through the Ethernet and radio interfaces of the AP. You can utilize both of these techniques to design the channels on the Aps:
- Web GUI
- CLI
This record clarifies how to utilize ACLs to design channels through the CLI. For data on the best way to design channels through the GUI, allude to Configuring Filters.
You can utilize the CLI to arrange these sorts of ACL-built channels in light of the AP:
- Channels that utilize standard ACLs
- Channels that utilize augmented ACLs
- Channels that utilization MAC address ACLs
The quantity of permitted sections on an ACL is restricted by the CPU of the AP. In the event that there is an extensive number of passages to add to an ACL, for example when separating a rundown of MAC locations for the customers, utilize a switch as a part of the system that can perform the undertaking. You can utilize standard ACLs to permit or prohibit the entrance of customer gadgets into the WLAN system focused around the IP location of the customer. Standard ACLs think about the source location of the IP bundles to the addresses that are arranged in the ACL so as to control activity. This sort of ACL could be alluded to as a source IP location based ACL. Standard ACLs can additionally utilize the stretched out scope of 1300 to 1999. These extra numbers are extended IP ACLs. At the point when a standard ACL is arranged to deny access to a customer, the customer still partners to the AP. Be that as it may, there is no information correspondence between the AP and the customer.
This sample demonstrates a standard ACL that is designed to channel the customer IP address 10.0.0.2 from the remote interface (radio0 interface). The IP location of the AP is 10.0.0.1. After this is carried out, the customer with IP address 10.0.0.2 can't send or get information through the WLAN system despite the fact that the customer is related to the AP. Complete these steps with a specific end goal to make a standard ACL through the CLI:
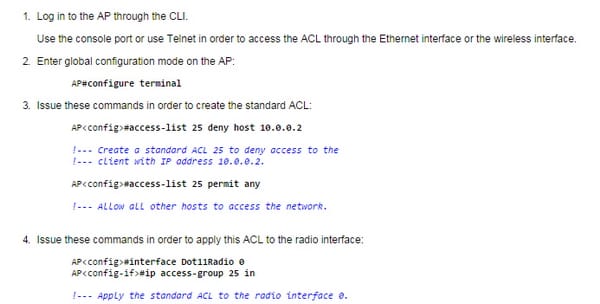
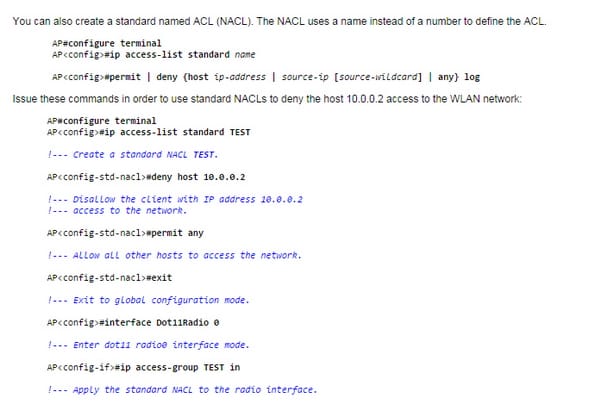
For MAC based ACL, see the following figure;
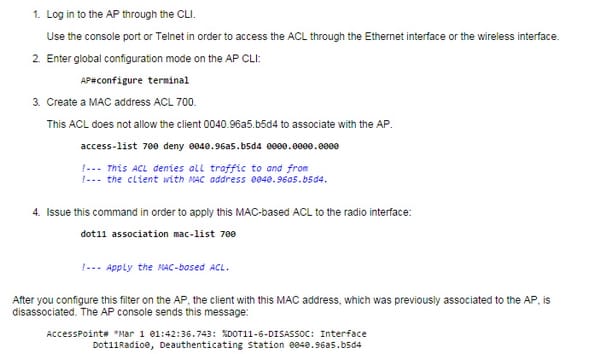
Access control records are a standard component in securing your systems and comprehension their capacity and fitting arrangement is vital to accomplishing their best viability. Confirmation preparing spreads ACLs and there are a few inquiries on exams that worry them. As we proceed in this arrangement, it would be savvy to test a percentage of the ideas on system test systems or unused switch ports to addition a superior point of view utilizing ACLs and how they may be spoken to in genuine usage and on the exams.
Site Search:






