- Home
- Popular IT Certifications
- Configure and Verify CLI for Router Configuration
How to Configure and verify utilizing the CLI to set basic Router configuration
The CLI is a content based interface for designing and observing HP switches and directing switches. You can access the CLI can through either an immediate serial association with the switch or steering switch or through a Telnet session. Here is the more information about CLI;
The command in the CLI is sorted out into the accompanying levels:
- User EXEC - Lets you show data and perform fundamental errands, for example, pings and follow courses.
- Privileged EXEC - Lets you utilize the same charges as those at the User EXEC level in addition to design commands that don't oblige sparing the progressions to the framework config document.
- CONFIG - Lets you roll out setup improvements to the gadget. To spare the progressions crosswise over reboots, you need to spare them to the framework config document. The CONFIG level contains sub-levels for individual ports, for VLANS, for directing conventions, and other areas of configuration.
Hostname:
In machine organizing, a hostname is a mark that is allocated to a gadget joined with a machine system and that is utilized to distinguish the gadget in different types of electronic correspondence, for example, the World Wide Web, email or Usenet. Hostnames may be straightforward names comprising of a solitary word or expression, or they may be structured. On the Internet, hostnames may have affixed the name of a Domain Name System (DNS) area, differentiated from the host-particular mark by a period ("spot"). In the last structure, a hostname is additionally called a space name. On the off chance that the area name is totally indicated, including a top-level space of the Internet, then the hostname is said to be a completely qualified area name (FQDN). Hostnames that incorporate DNS spaces are frequently put away in the Domain Name System together with the IP address of the host they speak to with the end goal of mapping the hostname to anaddress, or the converse process. Hostnames are comprehensible monikers that compare to the address of a gadget associated with a system. They are utilized by different naming frameworks, e.g., Network Information Service (NIS), Domain Name System (DNS), Server Message Block (SMB), and the significance of hostname will shift as indicated by the naming framework utilized. A hostname compelling to a Microsoft NetBIOS workgroup may be an invalid Internet hostname. At the point when introduced with a hostname without any setting, it is generally protected to expect that the system is the Internet and the hostname's naming framework is the DNS. Host names are normally utilized within an authoritative limit and may show up in machine program records, dynamic registry records, IP address to hostname resolutions, email headers, etc. On the Internet, a hostname is a space name allocated to a host machine. This is generally a combo of the host's neighborhood name with its parent area's name. Case in point, en.wikipedia.org comprises of a nearby hostname and the area name wikipedia.org. This sort of hostname is deciphered into an IP address by means of the nearby has record, or the Domain Name System (DNS) resolver. It is feasible for a solitary host machine to have a few hostnames; yet by and large the working arrangement of the host likes to have one hostname that the host utilizes for it. Any area name can additionally be a hostname, the length of the limitations said beneath are emulated. Thus, for instance, both en.wikipedia.org and wikipedia.org are hostnames in light of the fact that they both have IP address appointed to them. The area name pmtpa.wikimedia.org is not a hostname since it doesn't have an IP address (starting now), however rr.pmtpa.wikimedia.org is a hostname. A hostname may be a space name, on the off chance that it is legitimately composed into the area name framework. An area name may be a hostname on the off chance that it has been allocated to an Internet have and connected with the host's IP address.
Local user and password:
In more diminutive systems, or systems that have a couple of system directors, when you log into a Cisco gadget you are incited for a watchword. This will take you to the Router> brief where more than likely you will quickly sort "enable" to enter into special executive mode, and you will be provoked with a secret key again to get to favored executive mode or 'enable mode'. This for the most part works fine for more diminutive organizations and organizations without an excess of directors and the enable secret word would be imparted amongst them.in bigger associations a more granular methodology is regularly required and more control is obliged to distinguish diverse levels of authorizations for each of the clients that may join with a Cisco gadget. This necessity needs every client to login to a Cisco gadget with their own particular username and watchword, and each one record made will be appointed an alternate level of authorization on the device's request to arrange this on a Cisco gadget, usernames and passwords need to be made on the gadget and every client account must be related a benefit level. Moreover, each of the lines that may be utilized to get to the switch (Console, VTY, AUX) needs to be arranged to utilize the neighborhood client accounts database on the switch for validation. The following is the arrangement to arrange two client accounts (jay and bounce) unified with level 15 rights to gain entrance and the other with level 1.
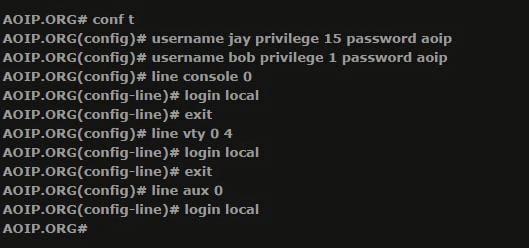
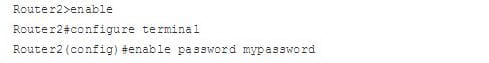
Enable secret password:
You utilize the enable secret password each time you move from User EXEC mode to Privileged EXEC mode. This secret key provides for you security on your switch, in light of the fact that Privileged EXEC mode is the place all the risky orders are found, including access to Global Configuration mode. To set an enable secret key, utilize the accompanying command:
Console & VTY logins:
The utilization of secret key security to control or confine access to the order line interface (CLI) of your switch is one of the basic components of a general security plan. Ensuring the switch from unapproved remote access, normally Telnet is the most widely recognized security that needs arranging, yet securing the switch from unapproved neighborhood access can't be neglected.
Note: Password insurance is only one of the numerous steps you ought to use in a compelling top to bottom system security regimen. Firewalls, access-records, and control of physical access to the gear are different components that must be considered when executing your security plan.
Command line, or EXEC, access to a switch might be made in various routes, yet in all cases the inbound association with the switch is made on a TTY line. There are four primary sorts of TTY lines, as seen in this specimen show line yield:
The CTY line-sort is the Console Port. On any switch, it shows up in the switch design as line con 0 and in the yield of the show line command as CTY. The comfort port is essentially utilized for neighborhood framework access utilizing a support terminal. The TTY lines are no concurrent lines utilized for inbound or outbound modem and terminal associations and might be seen in a switch or access server design as line x. The particular line numbers are a capacity of the fittings based into or introduced on the switch or access server. The AUX line is the Auxiliary port, seen in the setup as line aux 0. The VTY lines are the Virtual Terminal lines of the switch, utilized singularly to control inbound Telnet associations. Each of these sorts of lines could be arranged with secret word security. Lines could be arranged to utilize one watchword for all clients, or for client particular passwords. Client particular passwords could be designed by regional standards on the switch, or you can utilize a validation server to give verification. There is no restriction against designing distinctive lines with diverse sorts of secret key insurance. It is, truth is told, regular to see switches with a solitary watchword for the comfort and client particular passwords for other inbound associations.
Exec-timeout:
The EXEC timeout is an essential Cisco IOS setting that you will need to be mindful of when designing your Cisco gadget to permit client access. By setting the EXEC timeout, you're advising the Cisco gadget to consequently detach clients on a line once they have been unmoving for the length of time of the EXEC timeout esteem. This peculiarity is designed on a line-by-line premise and permits the Cisco gadget to naturally clear lines so they are accessible to different clients. It likewise goes about as a straightforward security instrument so an unattended terminal session can timeout before it turns into an open entryway to imaginative system reconfiguration.
Service password encryption:
This is utilized for scrambling all your passwords so they can't be effortlessly perused by people viewing you arranges the switch over your shoulder. It is a considerable measure better having the passwords not show clear content as then other individuals who don't have to be getting to the switch still don't have the foggiest idea. Presently, you would prefer not to be passing around your config to everybody on the grounds that in the event that they get the config and duplicate/ glue the secret key, even with administration watchword encryption enabled, it will be effortlessly crack able in numerous sites. The main secure way is utilizing password encryption.
Interface IP Address:
An Interface address is an interface (system) address, is simply a system deliver that fits in with an interface. In spite of the fact that practically all fit in with an interface on the off chance that they're being utilized. The term you've utilized raises an essential point. Just about all system addresses e.g. IP address, have a place with a system interface. Any gadget with an IP Address has an IP Address on an interface.
A system interface is the hardware of the part where the system link joins with - the controller there. NIC stands for system interface controller or system interface (controller) card. WNIC is remote system interface controller or remote system interface (controller) card. IP Addresses fit in with system interfaces, not to the machine itself. You don't ping a machine, you ping a machine's system interface. Regardless of the possibility that you ping 127.0.0.1 is known as the loopback interface. A machine could have a NIC with numerous Ethernet attachments, numerous system interfaces and every unified with an alternate IP Address, see the IP Address fits in with an interface. Also electronically, on the off chance that you ping a machine, you're really pinging specifically, the system interface on the machine. There aren't numerous cases of IP Addresses that don't fit in with an interface. An IP Address you haven't allocated to an interface (so it isn't relegated to a gadget, in light of the fact that IPs aren't precisely appointed to gadgets, just to interfaces of gadgets). The system address I assume does not and even can't fit in with any interface What's more the telecast address e.g. 255.255.255.255 intended to be sent to all interfaces, no interface would have that address.
(i) loopback
It alludes to the directing of electronic indicators, advanced information streams, or streams of things once again to their source without purposeful handling or adjustment. This is principally a method for testing the transmission or transportation foundation.
Numerous illustration applications exist. It might be a correspondence channel with standout correspondence endpoint. Any message transmitted by such a channel is instantly and just gotten by that same channel. In information transfers, loopback gadgets perform transmission tests of access lines from the serving exchanging focus, which normally does not require the aid of staff at the served terminal. Circle around is a technique for testing between stations that are not so much neighboring, where in two lines are utilized, with the test being carried out at one station and the two lines are interconnected at the removed station. A patch link might additionally work as loopback, when connected physically or consequently, remotely or provincially, encouraging a circle back test.
Banner:
In the connection of Computer Networking, Banner Grabbing is a count system used to gather data about machine frameworks on a system and the administrations running its open ports. Heads can utilize this to take stock of the frameworks and administrations on their system... A gatecrasher however can utilize flag getting as a part of request to discover system has that are running forms of uses and working frameworks with known exploits. Some samples of administration ports utilized for standard snatching are those utilized by Hyper Text Transfer Protocol (HTTP), File Transfer Protocol (FTP), and Simple Mail Transfer Protocol (SMTP); ports 80, 21, and 25 individually. Apparatuses usually used to perform flag getting are Telnet, which is incorporated with most working frameworks, and Net cat.
MOTD:
At the point when arranged, a message of the day (MOTD) standard shows a designed message to all uniting terminals. In this area, you will design a MOTD standard on R1 that demonstrates which switch you have joined with that is, "This is Router 1." To do thus, enter worldwide setup mode and issue the accompanying order, took after by a delimiting character. Here is the command line for it;
Copy runs start:
Here is the command line for it;
Hence learning about CLI is very important since it can make someone know how the router and the switches can be verified and how they actually work in the real life networking when they are connected and are utilized.
Site Search:






