- Home
- Popular IT Certifications
- Cisco Switches: Basic Concepts and Operation
Describe the basic switching concepts and the operation of Cisco switches
A network switch is a machine organizing gadget that is utilized to join gadgets together on a machine system, by utilizing a manifestation of bundle switching to forward information to the end gadget. A system switch is viewed as more developed than a center point in light of the fact that a switch will just forward a message to one or different gadgets that need to get it, as opposed to TV the same message out of each of its ports. One must know about them all. Here is some information which can be useful for understanding the Cisco switches;
A system switch is a multi-port system connects that methodologies and advances information at the information connection (layer 2) of the OSI model. Switches can likewise consolidate directing notwithstanding crossing over; these switches are generally known as layer-3 or multilayer switches. Switches exist for different sorts of systems including Fiber Channel, Asynchronous Transfer Mode, Ethernet and others.
Collision Domains
A collision domain is a segment of a system where information parcels can have collision with each other while being sent on an imparted medium or through repeaters, especially when utilizing early forms of Ethernet. A system collision happens when more than one gadget endeavors to send a bundle on a system section in the meantime. Crashes are determined utilizing bearer sense numerous accesses with collision recognition (CSMA/CD) in which the contending parcels are disposed of and re-sent each one in turn. This turns into a wellspring of wastefulness in the network. Stand out gadget in the collision domain may transmit at any one time, and alternate gadgets in the space listen to the system with a specific end goal to evade information crashes. Since stand out gadget may be transmitting at any one time, aggregate system data transfer capacity is imparted among all gadgets. Crashes likewise abatement system productivity on a crash space; if two gadgets transmit at the same time, and collision happens, and both gadgets must retransmit at a later time. Since information bits are proliferated at a limited velocity, all the while is to be characterized as far as the measure of the collision domain and the base parcel size permitted. A more diminutive parcel size or a bigger measurement would make it feasible for a sender to wrap up the bundle without the first bits of the message having the capacity to achieve the most remote hub. In this way, that hub could begin sending too, without a sign to the transmission effectively occurring and wrecking the first bundle. Unless the measure of the collision space permits the starting sender to get the second transmission endeavor - the crash - inside the time it takes to send the bundle he would none, of these have the capacity neither to discover the collision nor to rehash the transmission - this is known as a late crash.
Collision spaces are found in a center point or repeater environment where each one host portion join with a center that speaks to stand out crash space inside one show area. Collision domains are likewise found in other imparted medium systems, e. g. remote systems, for example, Wi-Fi. Current wired systems utilize a system switch to wipe out crashes. By joining every gadget straightforwardly to a port on the switch, either each one port on a switch turns into it collision space (on account of half duplex connections) or the likelihood of collisions is wiped out totally on account of full duplex connections.
Broadcast Domains
A broadcast domain is a coherent division of a machine system, in which all hubs can achieve one another by telecast at the information connection layer. A telecast area could be inside the same LAN section or it might be crossed over to other LAN sections. Regarding current prominent innovations: Any machine joined with the same Ethernet repeater or switch is a part of the same telecast area. Further, any machine joined with the same set of between associated switches/repeaters is a part of the same show area. Switches and other higher-layer gadgets structure limits between telecast domains. This is as contrasted with a crash area, which would be all hubs on the same set of between associated repeaters, isolated by switches and learning extensions. Collision domain is for the most part more modest than, and contained inside, show spaces. While some layer two system gadgets can isolate the crash domain, telecast spaces are just isolated by layer 3 system gadgets, for example, switches or layer 3 switches. Differentiating VLANS partitions show spaces too, however gives no intends to system these without layer 3 functionality. The refinement in the middle of telecast and collision domain comes to fruition on the grounds that straightforward Ethernet and comparable frameworks utilize an imparted transmission framework. In straightforward Ethernet (without switches or extensions), information edges are transmitted to all different hubs on a system. Each one accepting hub checks the terminus location of each one edge, and basically overlooks any casing not tended to its own particular MAC.
Switches go about as cradles, getting and breaking down the edges from each one joined system section. Casings bound for hubs associated with the starting fragment are not sent by the switch. Edges bound for a particular hub on an alternate section are sent just to that fragment. Just show casings are sent to all different portions. This lessens unnecessary activity and collisions.
In such a switched system, transmitted edges may not be gotten by all other reachable hubs. Ostensibly, just show casings will be gotten by all different hubs. Collisions are confined to the system section they happen on. In this way, the telecast area is the whole between joined layer two system, and the fragments associated with each one switch/scaffold port are every collision space. Not all system frameworks or media peculiarity telecast/collision domain. Case in point, PPP joins.
Ways to switch
Both store-and-forward and cut-through Layer 2 switches build their sending choices in light of the end MAC location of information parcels. They additionally learn MAC addresses as they look at the source MAC (SMAC) fields of parcels as stations correspond with different hubs on the system.
At the point when a Layer 2 Ethernet switch launches the sending choice, the arrangement of steps that a switch experiences to figure out if to forward or drop a bundle is the thing that separates the cut-through technique from its store-and-forward partner. While a store-and-forward switch settles on a sending choice on an information parcel after it has gotten the entire casing and checked its respectability, a cut-through switch takes part in the sending process not long after it has analyzed the end MAC (DMAC) location of an approaching edge. In principle, a cut-through switch gets and looks at just the initial 6 bytes of an edge, which conveys the DMAC address. On the other hand, for various reasons, as will be demonstrated in this record; cut-through switches hold up until a couple of more bytes of the edge have been assessed before they choose whether to forward or drop the parcel.
I. Store
It means that the LAN switch duplicates each one complete casing into the switch memory supports and figures a cyclic repetition check (CRC) for lapses. CRC is a lapse checking strategy that uses a numerical equation, in light of the quantity of bits (1s) in the edge, to figure out if the casing has error. In the event that a CRC mistake is discovered, the edge is tossed. In the event that the edge is lapse free, the switch advances the casing out the fitting interface port.
II. Forward
This kind of switching will hold up until the whole edge has landed before forwarding it. This system saves the whole edge in memory. Once the frame is in memory, the switch checks the end of the line address, source address, and the CRC. On the off chance that no slips are available, the edge is forwarded to the proper port. This procedure guarantees that the destination system is not influenced by tainted or truncated frames. It implies that the LAN switch duplicates each one complete casing into the switch memory cradles and figures a cyclic repetition check (CRC) for blunders. CRC is a slip checking strategy that uses a scientific equation, taking into account the quantity of bits (1s) in the casing, to figure out if the edge has error. In the event that a CRC slip is discovered, the casing is tossed. On the off chance that the edge is lapse free, the switch advances the casing out the proper interface port.
III. Cut through
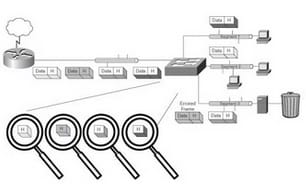
With cut-through switching, the LAN switch duplicates into its memory just the terminus MAC address, which is spotted in the initial 6 bytes of the edge after the introduction. The switch finds the goal MAC address in its switching table, decides the cordial interface port, and advances the casing on to its end through the assigned switch port. A cut-through switch diminishes delay on the grounds that the switch starts to forward the edge when it peruses the objective MAC address and decides the friendly switch port. Cut-Through switching will begin forwarding the casing when the end of the line location is identified. The distinction in the middle of this and Store-and-Forward is that Store-and-Forward gets the entire casing before forwarding. Since outline slips can't be recognized by perusing just the destination location, Cut-Through may effect system execution by forwarding undermined or truncated casings. These terrible edges can create show storms wherein a few gadgets on the network respond to the ruined casings at the same time.
Outlines with and without blunders are sent in cut-through switching operations, leaving the lapse location of the edge to the planned beneficiary. On the off chance that the getting switch decides the casing is eroded, the edge is tossed out to the bit can where the edge is consequently disposed of from the network. Cut-through switches don't perform any slip checking of the casing on the grounds that the switch searches just for the outline's end of the line MAC address and advances the edge out the suitable switch port. Cut-through switching brings about low switch idleness. The downside, notwithstanding, is that awful information outlines, and additionally great edges, are sent to their ends of the line. At the outset, this may not sound awful in light of the fact that most system cards do their own particular edge checking of course to guarantee great information is gotten. You may find that if your system is broken down into workgroups, the probability of awful edges or crashes may be minimized, thus making cut-through switching a decent decision for your system.
CAM Table
An Ethernet switch's part is to duplicate Ethernet outlines starting with one port then onto the next. The vicinity of a CAM table is one trait that differentiates a change from a center point. Without a practical CAM table, all edges got by a system switch would be reverberated vacate to all different ports, much like an Ethernet center point. A switch ought to just radiate an edge on the port where the end system gadget lives (unicast), unless the casing is for all hubs on the switch (telecast) or different hubs (multicast). By and large, the CAM table is a framework memory build utilized by Ethernet switch rationale to diverse Media Access Control (MAC) locations of stations to the ports on which they associate with the switch. This permits switches to encourage correspondences between joined stations at high velocity paying little heed to what number of gadgets are associated with the switch. The CAM table is counseled to settle on the casing sending choice. Switches take in MAC addresses from the source location of Ethernet casings on the ports, for example, Address Resolution Protocol reaction packets. Cam tables are frequently the focus of layer 2 system assaults in a neighborhood to set up man-in-the-center assaults. A risk operator which has control of a gadget joined with an Ethernet switch can assault the switch's CAM table. This assault generally includes abusing powerlessness in switch plan that shows up when the switch uses up space to record the majority of the MAC location to port mappings it learns. In the event that the table tops off because of MAC flooding, most switches are no more equipped to dependably include new MAC addresses.
Hence one can know by reading this all that how important a cisco switch is. Also, the switch can perform many functions which one must know so that he can know how the networks work and how they can be used in more beneficial way.
Site Search:






