- Home
- Popular IT Certifications
- Verify Router Configuration, Network Connectivity
How to verify router configuration and network connectivity using ping, traceroute, telnet, SSH and sh cdp neighbors
A router is a systems administration gadget and specific equipment that advances information packets between machine systems. This makes an overlay internetwork, as a router is associated with two or more information lines from diverse systems. At the point when an information bundle comes in one of the lines, the router peruses the location data in the packets to focus its extreme objective.
At that point, utilizing data within its routing table or routing approach, it controls the bundle to the following system on its voyage. Routers perform the "activity coordinating" works on the Internet. An information packet is ordinarily sent starting with one router then onto the next through the systems that constitute the internetwork until it achieves its terminus node. The most commonplace kind of routers are home and little office routers that essentially pass information, for example, site pages, email, IM, and features between the home machines and the Internet. A case of a router would be the holder's link or DSL router, which associate with the Internet through an ISP. More refined routers, for example, endeavor routers, join expansive business or ISP systems up to the compelling center routers that forward information at fast along the optical fiber lines of the Internet spine. In spite of the fact that routers are ordinarily committed fittings gadgets, utilization of programming based routers has developed progressively normal.
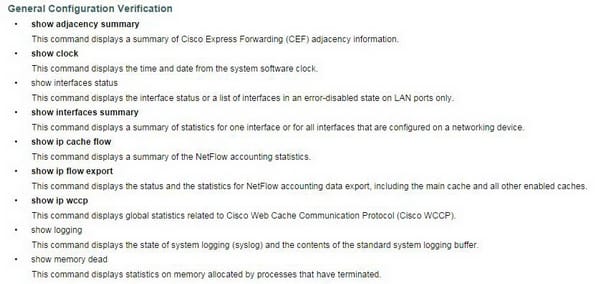
There are many commands which can be used for the configuration and some of them are shown in this screen shot.
Ping
It is the name of a standard programming utility (apparatus) used to test system associations. It might be utilized to figure out whether a remote gadget, (for example, Web or amusement server) could be arrived at over the system and, assuming this is the case, the association's dormancy. Ping apparatuses are some piece of Windows, Mac OS X and Linux and a few routers and amusement consoles. The term "ping" is additionally utilized conversationally by machine devotees when starting contact with someone else by means of email, text or other online instruments.
Short for Packet Internet Groper, ping is a utility used to check whether a system information bundle is fit for being appropriated to a location without lapses. The ping utility is usually used to check for system mistakes.
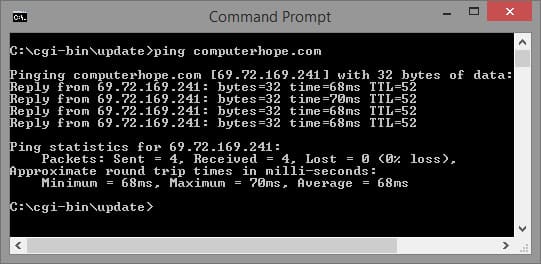
The picture is an illustration of what happens when a ping is sent. As might be seen, the client would first begin by utilizing the ping order to ping the IP address 204.228.150.3. Next, the solicitation is sent over the system center point and router, in this fundamental sample, to the next machine with this IP address. When effectively got, the machine answers to the ping with a pong reaction. The time between these two transmissions is computed to create a normal reaction or dormancy time. This sample is a case of the Windows charge line ping order we are pinging "computerhope.com" and get 4 reactions from the server. On the off chance that the ping does not achieve its objective, either because of system setup slip or in light of the fact that it is, no doubt hindered, the sending machine experiences a solicitation timed out mistake or demonstrates no got bundles.
It is system organization utility used to test the reachability of a host on an Internet Protocol (IP) system and to measure the round-excursion time for messages sent from the starting host to an end of the line machine. The name originates from dynamic sonar phrasing which sends a beat of sound and listens for the reverberation to recognize objects submerged.
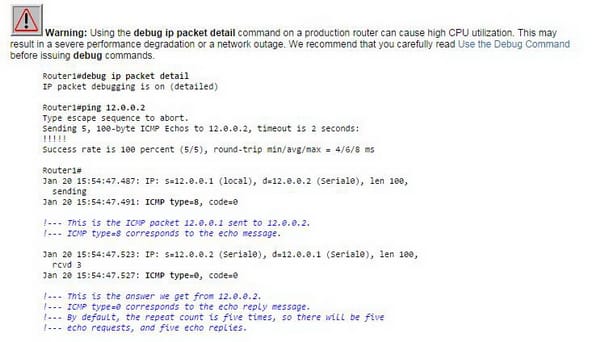
Ping works by sending Internet Control Message Protocol (ICMP) reverberation demand packets to the target have and sitting tight for an ICMP reaction. Simultaneously it measures the time from transmission to gathering (round-excursion time) and records any bundle misfortune. The aftereffects of the test are printed as a measurable outline of the reaction bundles got, including the base, most extreme, and the mean round-outing times, and here and there the standard deviation of the mean. Depending on genuine usage, the ping utility may be executed with different order line routers to empower unique operational modes. Case in point, choices incorporate detailing the packets size of the test, programmed rehashed operation for sending a detailed tally of tests, and time stamping. Numerous working frameworks give a sidekick utility, ping6, for testing Internet Protocol form 6 (Ipv6) has, however a few frameworks may incorporate this ability inside the ping utility. Ping may be ill-used as a straightforward type of dissent of-administration assault as a ping surge, in which the assailant overpowers the exploited person with ICMP reverberation demand packets. For debugging in Pings, use the following commands;
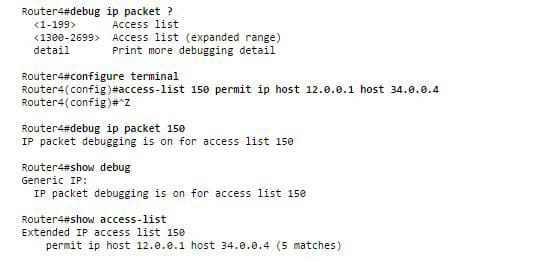
Extended
The Linksys brand, which is currently claimed by Cisco, fabricates a line of remote routers that can make a nearby Wi-Fi organize in your little business office. In the event that the router's remote sign is not arriving at all zones of the workplace, you may need to consider broadening it by including an alternate Linksys router. Put the second router into repeater mode and it will associate with the essential router's sign, augmenting the system to different zones.
Step 1
Open a Web program on any machine associated with your nearby remote system and sort "192.168.1.1" (without quotes) in the location bar.
Step 2
Log into the router's page, with the username and the password. In the event that you have never set a username or secret key, leave the Username field clear and enter "administrator" as the watchword.
Step 3
Go to the "Status" tab at the highest point of the page and click on the "Remote" join.
Step 4
Duplicate the arrangement of numbers and letters in the MAC Address field.
Step 5
Turn off your machine's remote card. Unite the auxiliary Linksys router to your machine utilizing an Ethernet link and backtrack to the 192.168.1.1 Web page.
Step 6
Go to the "Setup" tab at the highest point of the page and click on the "AP Mode" join.
Step 7
Select the "Remote Repeater" radio catch.
Step 8
Put the MAC location of the essential router into the "Remote Access Point's LAN MAC Address" field.
Step 9
Click the "Save" button.
Traceroute
Traceroute is a computer diagnostic device for showing the route (way) and measuring travel deferrals of bundles over an Internet Protocol (IP) system. The historical backdrop of the route is recorded as the round-outing times of the parcels got from every progressive host (remote hub) in the route (way); the whole of the interims in each one bounce demonstrates the aggregate time used to make the association. Traceroute moves ahead unless each of the (three) sent bundles are lost more than twice, then the association is lost and the route can't be assessed. Ping, then again, just registers the last round-trek times from the terminus point.
The traceroute order is accessible on various current working frameworks. On Apple Mac OS, it is accessible by opening 'System Utilities' then selecting "Traceroute" tab, and also by writing the "traceroute" charge in the terminal. On other UNIX frameworks, for example, FreeBSD or Linux, it is accessible as a traceroute order in a terminal. On Microsoft Windows, it is named tracer. Windows NT-based working frameworks additionally give Pithing, with comparable usefulness. For Internet Protocol Version 6 (Ipv6) the device once in a while has the name traceroute6 or tracert6. Traceroute, of route, sends a succession of User Datagram Protocol (UDP) bundles tended to an end of the line host; ICMP Echo Request or TCP SYN parcels can likewise be used. The time-to-live (TTL) esteem, otherwise called jump breaking point, is utilized within deciding the moderate routers being navigated towards the goal. Routers decrement bundles' TTL esteem by 1 when routing and dispose of parcels whose TTL esteem has arrived at zero, giving back where its due blunder message ICMP Time Exceeded. Regular default values for TTL are 128 (Windows OS) and 64 (Unix-based OS).traceroute lives up to expectations by sending parcels with bit by bit expanding TTL quality, beginning with TTL estimation of 1. The principal router gets the bundle, decrements the TTL esteem and drops the parcel on the grounds that it then has TTL quality zero. The router sends an ICMP Time Exceeded message once again to the source. The following set of parcels is given a TTL estimation of 2, so the first router advances the bundles, however the second router drops them and answers with ICMP Time Exceeded. Continuing thusly, traceroute utilizes the returned ICMP Time Exceeded messages to fabricate a rundown of routers that parcels navigate, until the end is arrived at and gives back an ICMP Echo Reply message. The timestamp qualities returned for every router along the way are the postponement (dormancy) values, normally measured in milliseconds for every bundle.
Telnet
Telnet is a system protocol utilized on the Internet or neighborhood to give a bidirectional intelligent content arranged correspondence office utilizing a virtual terminal association. Client information is sprinkled in-band with Telnet control data in an 8-bit byte turned information association over the Transmission Control Protocol (TCP).
Telnet was created in 1968 starting with RFC 15, reached out in RFC 854, and institutionalized as Internet Engineering Task Force (IETF) Internet Standard STD 8, one of the first Internet gauges. Telnet gave access to a summon line interface (ordinarily, of a working framework) on a remote host. Most system supplies and working frameworks with a TCP/IP stack help a Telnet administration for remote design (counting frameworks focused around Windows NT). Nonetheless, on account of genuine security issues when utilizing Telnet over an open system, for example, the Internet, its utilization for this reason has melted away significantly for SSH. The term telnet might likewise allude to the product that actualizes the customer piece of the protocol. Telnet customer applications are accessible for all intents and purpose all machine stages. Telnet is likewise utilized as a verb. To telnet intends to make an association with the Telnet protocol, either with order line customer or with an automatic interface. Case in point, a typical order may be: "To change your secret key, telnet to the server, log in and run the password charge." Most regularly, a client will be telnet ting to an Unix-like server framework or a system gadget, (for example, a router) and acquiring a login brief to a summon line content interface or a character-based full-screen manager. When Telnet was at first created in 1969, most clients of arranged machines were in the machine branches of scholastic organizations, or on the loose private and government research offices. In nature's turf, security was not about to the extent that worries as it got to be after the data transmission blast of the 1990s. The ascent in the quantity of individuals with access to the Internet, and by augmentation the quantity of individuals endeavoring to hack other individuals' servers, made scrambled choices vital.
SSH
Secure Shell (SSH) is a cryptographic system protocol for secure information correspondence, remote summons line login, remote order execution, and other secure system benefits between two organized machines. It joins, by means of a safe channel over an unstable system, a server and a customer running SSH server and SSH customer programs, separately. The protocol detail recognizes two real forms that are alluded to as SSH-1 and SSH-2.the best-known application of the protocol is for access to shell accounts on Unix-like working frameworks, yet it can likewise be utilized as a part of a comparable design for records on Windows. It was composed as a trade for Telnet and other unstable remote shell protocols, for example, the Berkeley rsh and rexec protocols, which send data, eminently passwords, in plaintext, rendering them vulnerable to capture and exposure utilizing bundle examination. The encryption utilized by SSH is planned to give secrecy and uprightness of information over an unsecured system, for example, the Internet.
SSH is normally used to log into a remote machine and execute summons, however it additionally backings burrowing, sending TCP ports and X11 associations; it can router records utilizing the related SSH record router (SFTP) or secure duplicate (SCP) protocols. SSH utilizes the customer server model. The standard TCP port 22 has been allocated for reaching SSH servers.
A SSH customer system is commonly utilized for making associations with a SSH daemon tolerating remote associations. Both are generally show on most present day working frameworks, including Mac OS X, most appropriations of GNU/Linux, Openbsd, Freebsd, Netbsd, Solaris and Openvms. Eminently, Windows is one of the few cutting edge desktop/server Oss that does exclude SSH naturally. Exclusive, freeware and open source renditions of different levels of unpredictability and fulfillment exist. Local Linux document supervisors can utilize the FISH protocol to give a part sheet GUI with move and customize. The open source Windows program Winscp gives comparative document administration (synchronization, duplicate, remote erase) ability utilizing Putty as a back-end. Both Winscp and Putty are accessible bundled to run specifically off of a USB drive, without obliging establishment on the customer machine. Setting up a SSH server in Windows ordinarily includes establishment.
SH CDP neighbors
Here is the command for CDP:
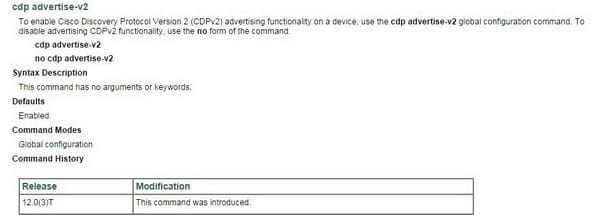
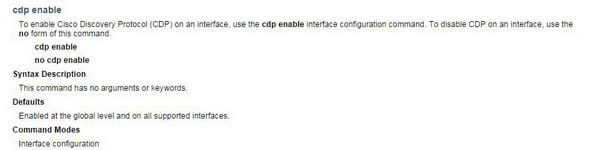
To enable CDP, use the following command:
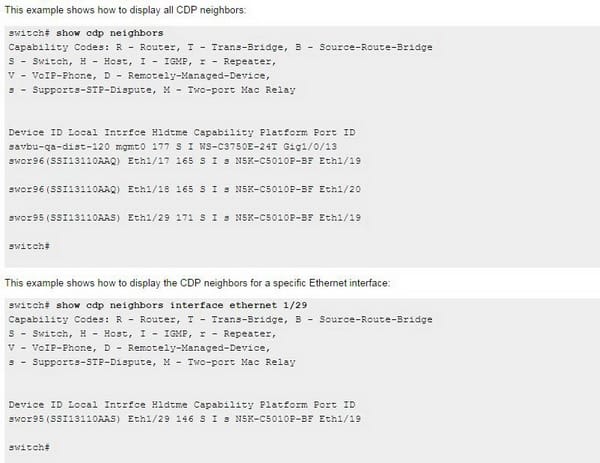
The command for showing the CDP neighbors is as follows;
Only having router at home isn't the main thing, but knowing about how to configure it and the meaning of the terminologies like telnet and ping etc. is, is more important.
Site Search:






