- Home
- Popular IT Certifications
- Routing Protocol Types & Concepts
Routing protocol types & concept of administrative distance
The routing protocols are created for the routers. These protocols are designed to permit the exchange of the routing tables or the known networks between the routers. There are a variety of routing protocols based on the specific network. The administrative distance helps to select the best path when 2 or more routes to a same destination from the 2 different routing protocols. Let us see more about the routing protocol types and the concepts of the administrative distance in the coming section.
3.5 Evaluate routing protocol types
Regarding to recent scenario, the routing protocol has become very pervasive. As the technology grows rapidly, the routing protocols become more popular among the recent technology. The routing protocols learns path for the IP, IPX, routed protocol and the Appletalk are the best examples of the routed protocols. The routing protocols running in the different routers exchange updates between each other and also most efficient routes to the destination. It has the capability to learn about the network when the new network is added and also detect when the networks becomes unavailable. It normally runs only in the routers, end devices,network servers or layer 3 switches with the network operating systems. The routing protocol is not available in the normal printer or a computer. The examples of the routing protocols are RIP, EIGRP, OSPF.
The routing protocol indicates how the routers communicate with one another, disseminating information which enables it to select the routes between any of the 2 nodes on the computer network. The routing protocol will share the information among the immediate neighbor first and then throughout the network. In this way, the routers acquire knowledge of the network topology.
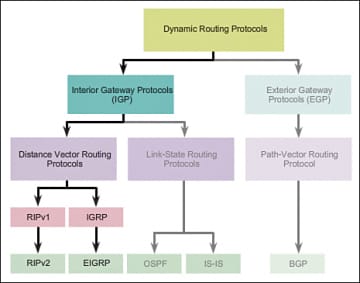
Although there are many widespread routing types, distance vector, link state and path vector are discussed below. The distance vector routing protocol and link state routing protocol come under the interior gateway protocols and the path vector routing protocols comes under the exterior gateway protocols.
3.5.a Distance vector
The distance vector is one among the routing protocol. It uses the Ford Fulkerson algorithm, Bellman ford algorithm or the DUAl FSM (for Cisco) calculate the paths. The neighbors are the routers which share the link and that are configured to use a same routing protocol. A router is the only one aware of a network address of its own interface as well as a remote network address, it will reach via its neighbor. The routers with uses the distance vector routing will never aware of a network topology. The best examples of the distance vector routing protocols are such as:
Interior gateway routing protocol
The metric of the IGRP are such as reliability, delay, load and bandwidth and the routing update sent is 90 seconds.
Routing information protocol (version 1 &2)
The metric of the RIP is hop count and the routing update sent is 30 seconds.
Enhanced interior gateway routing protocol
The metric of the EIGRP is the proprietary protocol and hybrid. The routing update sent is a topology change triggers.
The periodic updates of the distance vector routing protocol is 30 to 90 seconds and the broadcast updates are 255.255.255.255.
The entire routing table is included with the routing table. The distance vector routing protocol just requires less maintenance and simple implementation only. The level of knowledge needs to deploy and also maintain the network with this protocol is not so high like other protocols. It typically do not require a large number of memory to save the information and nor do they need the powerful central processing unit. Based on the network size and an IP addresses implemented, it typically do not need the high level of link bandwidth to send the routing updates. Anyway, it can become the problem if the distance vector protocol is deployed in the large network.
The use of a periodic update will cause the slow convergence in this protocol. However, if some of the advanced techniques are used such as the triggered updates. The overall convergence is slow when compared to the link state routing protocols. The slow convergence can limit the network size, because the larger networks need much time to propagate the routing information. The routing loops will occur when the inconsistent routing table is not updated due to the slow convergence in the changing network. The core of the distance vector protocol is a routing algorithm. This algorithm is widely used to calculate the paths and this algorithm is defined in the following processes are:
Mechanism for sending and also receiving the routing information
Mechanism for calculating the paths and also installing routes in a routing table.
Mechanism for identifying and reacting to the topology changes.
Different routing protocols will use different algorithms to install the routes in a routing table and sends updates to the neighbors and also make path determination decisions.
3.5.b Link state
The link state routing protocol is the major class of the routing protocols used in the packet switching network for the computer communications. The best example of the link state routing protocol is IS-IS (intermediate system to intermediate system) and OSPF( open shortest path first.
The link state protocol is performed by each switching node in a network. The main concept of this protocol is that each node constructs the map of the connectivity to a network, which nodes are connected with other nodes. Every node will independently calculate a next logical path from that to each possible destination in a network. This collection of the best path will form the node routing table. The link state packet, or the link state advertisement is the small packet of the routing information which is sent in between the routers. The SPF algorithm is the calculation performed on a database which results in an SPF tree. The link state database or topological database is the collection of the information which is gathered from the LSAs.
In the link state routing algorithm, each router has the responsibility for meeting its neighbors as well as learning its names. It used the Hello protocol, that send the data packet contains RID and the network address on which the packets are being sent.
Each router constructs the LSA or LSP which is comprised of the cost for every neighbor and list of names. The LSA/LSP is transmitted to the entire routers. Each router saves the very recently generated LSA/LSP from the every other router. The Dikjstra's algorithm is also known as the SPF - shortest path first algorithm.
In the process, the routers will first learn of directly connected networks, after that the routers will say hello to neighbors which will link the state packets. Then the routers flood the LSP to all the neighbors. Finally, the routers use the LSP database to build the network topology map and also to calculate the perfect path to each destination. After initial flooding, the additional LSP will send out when the change in the topology occurs.
3.5.c Path vector
The distance vector routing is subject to the instability if there is more than some hops in a domain operation. Link state routing requires the huge amount of the resources to calculate the routing tables. It creates heavy traffic due to flooding. For that, there is a need for the third routing protocol which is called as path vector.
The principle of the path vector is same to that of the distance vector routing. In the path vector routing protocol, there is one node in each of the autonomous system which acts on behalf of all autonomous systems which is called as speaker node. A speaker node in the AS creates the routing table and also advertises that to speaker nodes in the neighbor Ass. BGP (border gateway protocol) is the best example of the path vector protocol. In BGP, the routing table will maintain the autonomous systems which are traversed to reach the destination system. The path vector will not rely on cost of reaching the given destination to find whether each path in the loop free or not. It mainly relies on the analysis of the path to reach the destination.
This protocol is currently in the limelight, due to its inter domain routing protocol of the internet, BGP belong to this category.
3.6 Describe administrative distance
Most of the routing protocols have the metric structures as well as algorithms which are not at all compatible with the other protocol. In the network with multiple routing protocol, the capability to select the perfect path and exchange of the route information across the multiple protocol is very critical.
Administrative distance is the suitable feature that the routers will use to select the perfect path when there are 2 or more different routes to a same destination from the 2 different routing protocol. Generally, AD (administrative distance) is an arbitrary numerical value that assigned to the routing protocol. The AD value is used by the Cisco routers to find the best route which should be used in the multiple paths to the exist same destination. The routing protocol with the lower AD is better and provide priority for the routing protocol with higher AD. This AD value can be set manually by the network administrator. If the network administrator fails to set it properly, then the router will use the default AD.
The Ad defines a reliability of the routing protocol. Every routing protocol is prioritized to the least reliable using the Ad value. The below table shows the default AD value of the protocols.
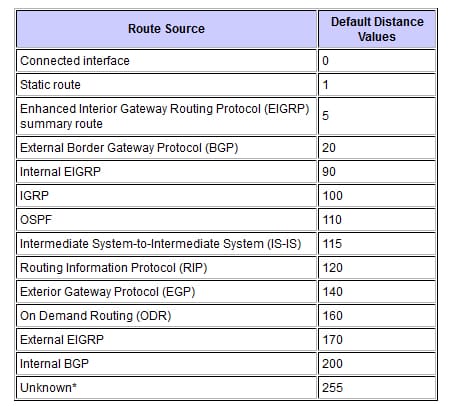
The administrative distance is the numeric value which ranges from 0 to 255. The smaller the AD is more trusted by the router, hence, the best AD being 0 and the far worst is 255. The AD is the initial criterion that the router uses to find which routing protocol to use, and if 2 protocols offer route information for a same destination. It is the measure of the source trustworthiness of a routing information. The AD has only the local significance and it is not advertised in the routing updates.
When the route redistribution is used, then it is required to change the AD of the protocol. Suppose, if you like to chose the RIP learned routers instead of IGRP learned routes to a same destination, then you has to decrease the AD of the RIP to less than 100 or increase the AD for the IGRP to 120+.
You can change the AD of the protocol via the distance command in a routing process of the sub configuration mode. Then this command indicates that the AD is assigned to a route learned from the specific routing protocol. When migrating the network from the one protocol to the other, use this procedure and later has the higher AD.
In some cases, the AD can lead to unexpected results or lead to being chosen which is not essential for the best route. It is true, if the routing destination is used on the router. In that case, the administrator would modify the AD manually, so that a desired routing protocols path takes the precedence over the other paths. The static routes can be used to offer the alternative path when the link fails. To configure the static routes as the backup, the static route's AD has to be adjusted. Or else, it will take the precedence over the entire routing protocol and the routes provided from the routing protocol cannot be inserted into a routing table.
The routing protocols are effectively distributed database systems. It propagates the information about the network topology among the routers within the network. The 3 main types of the routing protocols such as distance vector, link state and path vector widely used. By distributing the vector, it classified into distance vector and path vector and by means of distributing the state of the links, it is classified as a link state routing. Based on the needs and requirements of the network topology, those types of routing protocols are used. When there are 2 or more different routes on to the same destination, the Administrative distance is the one which helps to select the best path.
Site Search:






