- Home
- Popular IT Certifications
- How to Troubleshoot Device Access Control
Describe how to troubleshoot device access control
In the fields of physical security and data security, access control is the particular confinement of access to a spot or other resource. The demonstration of getting to may mean expending, entering, or utilizing. Consent to get to an asset is called authorization. Locks and login accreditations are two closely resembling components of access control.
Geological access control may be authorized by staff (e.g., fringe protect, bouncer, ticket checker), or with a gadget, for example, a turnstile. There may be fences to abstain from dodging this right to gain entrance control. An option of access control in the strict sense (physically controlling access itself) is an arrangement of checking approved vicinity, see e.g. Ticket controller (transportation). A variation is passageway control, e.g. of a shop (checkout) or a country.
The term access control alludes to the act of limiting passage to a property, a building, or a room to approved persons. Physical access control could be attained by a human (a watchman, bouncer, or assistant), through mechanical means, for example, bolts and keys, or through innovative means, for example, access control frameworks like the mantrap. Inside these situations, physical key administration might likewise be utilized as a method for further overseeing and checking access to mechanically keyed zones or access to certain little assets.
Physical access control is a matter of whom, where, and when. A right to gain entrance control framework figures out who is permitted to enter or passageway, where they are permitted to passageway or enter, and when they are permitted to enter or passageway. Generally, this was somewhat fulfilled through keys and locks. At the point when an entryway is bolted, just somebody with a key can enter through the entryway, contingent upon how the lock is designed. Mechanical bolts and keys don't permit confinement of the key holder to particular times or dates. Mechanical bolts and keys don't give records of the key utilized on any particular entryway, and the keys might be effectively duplicated or exchanged to an unapproved individual. At the point when a mechanical key is lost or the key holder is no more approved to utilize the ensured region, the locks must be re-keyed.
Electronic access control utilizes machines to unravel the impediments of mechanical bolts and keys. An extensive variety of qualifications could be utilized to supplant mechanical keys. The electronic access control framework awards access focused around the accreditation introduced. At the point when access is in all actuality, the entryway is opened for a foreordained time and the transaction is recorded. At the point when access is cannot, the entryway stay bolted and the endeavored access is recorded. The framework will likewise screen the entryway and caution if the entryway is constrained open or held open excessively long in the wake of being unlocked. when a qualification is exhibited to a pursuer, the pursuer sends the certification's data, normally a number, to a control board, a very solid processor. The control board contrasts the accreditation's number with a right to gain entrance control rundown, awards or denies the introduced ask for, and sends a transaction log to a database. At the point when access is denied focused around the right to gain entrance control list, the entryway stays bolted. On the off chance that there is a match between the qualification and the right to gain entrance control list, the control board works a transfer that thusly opens the entryway. The control board likewise disregards an entryway open sign to keep a caution. Frequently the pursuer gives criticism, for example, a blazing red LED for a right to gain entrance denied and a glimmering green LED for a right to gain entrance granted.
The above portrayal represents a solitary element transaction. Certifications could be passed. Passwords are a typical method for confirming a client's personality before access is given to data frameworks. What's more, a fourth variable of confirmation is presently remembered: somebody you know, whereby someone else who knows you can give a human component of verification in circumstances where frameworks have been set up to take into consideration such situations. Case in point, a client may have their secret key, however have overlooked their savvy card. In such a situation, if the client is known to assigned companions, the associates may give their savvy card and watchword, in consolidation with the surviving component of the client being referred to, and in this way give two variables to the client with the missing qualification, giving three components general to permit access. A certification is a physical/unmistakable article, a bit of information, or an aspect of an individual's physical being, that empowers an individual access to a given physical office or machine based data framework. Normally, accreditations could be something an individual knows, (for example, a number or PIN), something they have, (for example, a right to gain entrance marker), something they are, (for example, a biometric gimmick) or some mix of these things. This is known as multi-variable verification. The common qualification is a right to gain entrance card or key-coxcomb, and fresher programming can likewise transform clients' cell phones into access devices. There are numerous card innovations including attractive stripe, scanner tag, Wigand, 125 kHz closeness, 26-bit card-swipe, contact brilliant cards, and contactless savvy cards. Additionally accessible are key-dandies, which are more minimized than ID cards, and append to a key ring. Biometric innovations incorporate unique mark, facial distinguishment, iris distinguishment, retinal sweep, voice, and hand geometry. The inherent biometric advances found on more current cell phones can likewise be utilized as certifications within conjunction with access programming running on versatile devices.
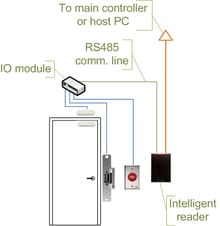
Access control choices are made by contrasting the certification with a right to gain entrance control list. This look-up is possible by a host or server, by a right to gain entrance control board, or by a pursuer. The improvement of access control frameworks has seen a consistent push of the look-up out from a focal host to the edge of the framework, or the pursuer. The look-up and control capacities are by the control board. The spokes impart through a serial association; generally RS-485. A few produces are pushing the choice making to the edge by setting a controller at the entryway. The controllers are IP empowered, and interface with a host and database utilizing standard networks. The most basic security danger of interruption through a right to gain entrance control framework is by essentially completing a real client an entryway, and this is alluded to as "tailgating". Regularly the real client will hold the entryway for the interloper. This danger could be minimized through security mindfulness preparing of the client populace, or more dynamic means, for example, turnstiles. In high security applications this danger is minimized by utilizing a sally port, in some cases called a security vestibule or mantrap, where administrator mediation is obliged apparently to guarantee substantial identification.
The second most regular danger is from levering an entryway open. This is shockingly straightforward and powerful on generally entryways. The lever could be as little as a screwdriver or enormous as a crow bar. Completely executed access control frameworks incorporate constrained entryway observing cautions. These differ in adequacy, generally falling flat from high false positive alerts, poor database design, or absence of dynamic interruption monitoring.
Like levering is smashing through shoddy parcel dividers. In imparted occupant spaces the divisional divider is helplessness. Defenselessness similarly is the breaking of sidelights. Satirizing locking equipment is decently basic and more exquisite than levering. A solid magnet can work the solenoid controlling jolts in electric locking equipment. Engine bolts, more common in Europe than in the US, are likewise helpless to this assault utilizing a doughnut molded magnet. It is additionally conceivable to control the ability to the lock either by evacuating or including current. Access cards themselves have demonstrated defenseless against refined assaults. Ambitious programmers have constructed convenient pursuers that catch the card number from a client's nearness card. The programmer basically strolls by the client, peruses the card, and after that introduces the number to a pursuer securing the entryway. This is conceivable on the grounds that card numbers are sent liberated, no encryption being used.
At last, most electric locking fittings still have mechanical keys as a fall flat over. Mechanical key locks are powerless against bumping.
Lines (VTY, AUX, console)
All Cisco switches have two exceptional sorts of lines, and numerous Cisco switches have a third. What are these lines, and how would you arrange them? These are things that each system administrator ought to know. "Lines" on Cisco switches are physical sync serial ports on the switch, (for example, a terminal or modem), a virtual system association, or an alternate sort of serial line on the switch. To see which lines you have on your switch, utilize the show line charge. Here's a sample:
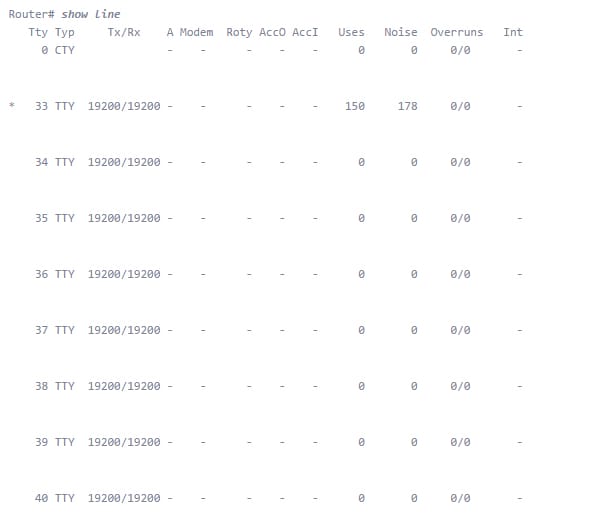
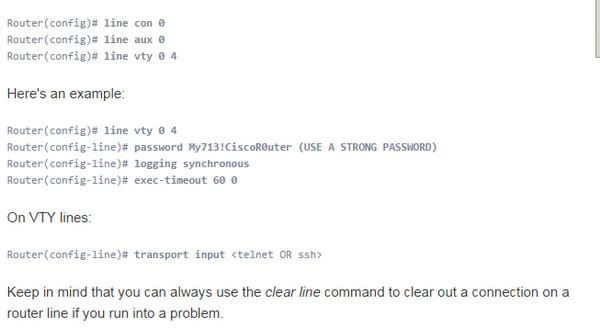
The support port shouldn't require any presentation. The CTY port is, obviously, where you arrange the switch when it's brand-new - before it has any IP address setup. The reassure port is a serial port, so you must have a PC/smart phone with a serial interface and unite with the comfort with a moved link, in all probability, utilizing a Db9 to Rj45 connector to associate from the serial port on your machine to the support port. When you've utilized the support port to arrange the switch's system setup, it isn't basic to need to utilize it once more. Nonetheless, it's great to realize that it's there if anything ever happens. Likewise, you ought to secure the reassure port to keep somebody from interfacing with it when you aren't around. VTY ports are virtual TTY ports, used to Telnet or SSH into the switch over the system. You can utilize them to join with the switch to roll out design improvements or check the status. Most switches have five VTY ports, numbered 0 to 4. That implies you can have up to five simultaneous system administrators designing the switch at one time. On the other hand, you can undoubtedly produce more VTY lines. While you could invest a great deal of time realizing all the arrangement varieties for lines on a Cisco switch, here's the least difficult and most helpful design for your switch lines.
Management plane protection
The Management Plane Protection (MPP) offer in Cisco IOS programming gives the ability to confine the interfaces on which arrange administration bundles are permitted to enter a gadget. The MPP gimmick permits a system administrator to assign one or more switch interfaces as administration interfaces. Gadget administration movement is allowed to enter a gadget just through these administration interfaces. After MPP is empowered, no interfaces with the exception of assigned administration interfaces will acknowledge system administration activity bound to the gadget.
Limiting administration parcels to assigned interfaces gives more prominent control over administration of a gadget, giving more security to that gadget. Different profits incorporate enhanced execution for information parcels on no management interfaces, help for system versatility, requirement for less get to control records (Acyls) to confine access to a gadget, and administration parcel surges on exchanging and directing interfaces are kept from arriving at the CPU. A control plane is a gathering of methods that run at the procedure level on a course processor and all things considered give abnormal state control for most Cisco IOS programming capacities. All movement specifically or by implication bound to a switch is taken care of by the control plane.
Password encryption
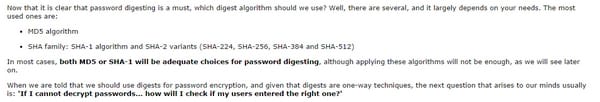
Practically all advanced web applications need, in somehow, to scramble their clients' passwords. We could say that, from the minute that an application has clients, and clients sign in utilizing a secret key, these passwords must be put away in a scrambled way. There are some natural explanations behind this: our information stores might be bargained, along these lines can our correspondences. Anyway the most essential reason is that we need to think about our clients' passwords as touchy individual information. Their passwords are their key to their security, so they are close to home, they are delicate, and nobody (not in any case us) has the right to know them. Furthermore we must respect this in the event that we need to increase our client's trust.
Site Search:






