- Home
- Popular IT Certifications
- Troubleshooting for IPv4 Addressing & Subnetting
Describe troubleshoot for IPv4 addressing and subnetting
There are two amendments of the IP convention that are broadly executed on frameworks today. Ipv4, which is the fourth form of the convention, right now is the thing that the lion's share of frameworks backing. The more up to date, sixth update, called Ipv6, is, no doubt took off with more noteworthy recurrence because of enhancements in the convention and the confinements of Ipv4 location space. Basically, the world now has an excess of web associated gadgets for the measure of locations accessible through Ipv4.
Ipv4 locations are 32-bit addresses. Every byte, or 8-bit fragment of the location, is isolated by a period and regularly communicated as a number 0-255. Despite the fact that these numbers are normally communicated in decimal to support in human appreciation, each one fragment is typically alluded to as an octet to express the way that it is a representation of 8 bits.
IPv4 Address Classes and the reserved range
IP locations are normally made of two different parts. The principal piece of the location is utilized to distinguish the system that the location is a part of. The part that comes subsequently is utilized to tag a particular have inside that system.
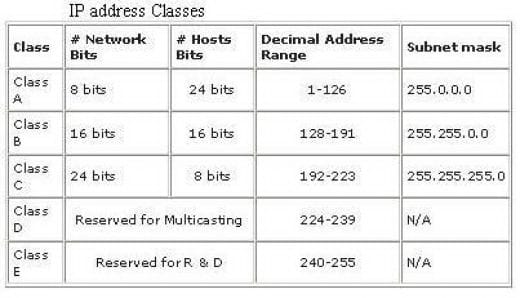
Where the system determination finishes and the host particular start relies on upon how the system is arranged. We will examine this all the more completely almost instantly. Ipv4 locations were generally partitioned into five separate "classes", named A through E, intended to separate sections of the accessible addressable Ipv4 space. These are characterized by the initial four bits of each one location. You can recognize what class an IP location has a place with by taking a gander at these bits.
Subnetting
A Class A, B, or C TCP/IP system might be further isolated, or subnetted, by a framework executive. This gets to be essential as you accommodate the coherent location plan of the Internet (the theoretical universe of IP locations and subnets) with the physical systems being used by this present reality.
A framework executive who is designated a square of IP locations may be managing systems that are not sorted out in a manner that effortlessly fits these locations. Case in point, you have a wide zone system with 150 hosts on three systems (in diverse urban areas) that are joined by a TCP/IP switch. Each of these three systems has 50 hosts. You are dispensed the class C system 192.168.123.0. (For outline, this location is really from an extent that is not designated on the Internet.) This implies that you can utilize the locations 192.168.123.1 to 192.168.123.254 for your 150 hosts.
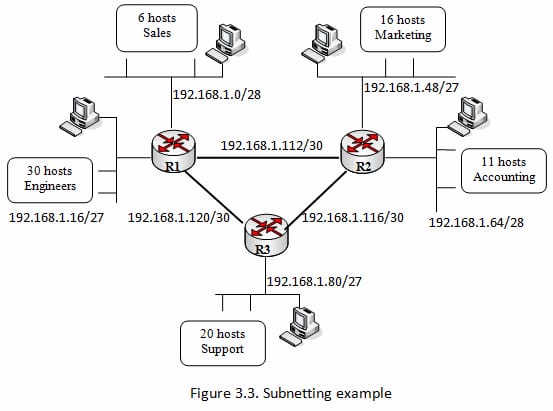
Two addresses that can't be utilized as a part of your sample are 192.168.123.0 and 192.168.123.255 in light of the fact that twofold locations with a host share of all ones and all zeros are invalid. The zero location is invalid on the grounds that it is utilized to determine a system without pointing out a host. The 255 location (in twofold documentation, a host location of all ones) is utilized to telecast a message to each host on a system. Simply recollect that the first and last address in any system or subnet can't be allocated to any individual host.
You ought to now have the capacity to give IP locations to 254 hosts. This works fine if each of the 150 machines are on a solitary system. On the other hand, your 150 machines are on three different physical systems. As opposed to asking for more address squares for each one system, you partition your system into subnets that empower you to utilize one square of locations on various physical systems.
Address types (Unicast, broadcast, multicast, and VLSM)
Every gadget on a system must be exceptionally characterized. At the Network layer, the bundles of the correspondence need to be related to the source and goal locations of the two end frameworks. With Ipv4, this implies that every bundle has a 32-bit source location and a 32-bit goal address in the Layer 3 header. These locations are utilized as a part of the information arrange as paired examples. Inside the gadgets, computerized rationale is petitioned their understanding. For us in the human system, a string of 32 bits is hard to decipher and significantly more hard to recall. Hence, we speak to Ipv4 locations utilizing spotted decimal organization.
For every Ipv4 address, some part of the high-request bits speaks to the system address. At Layer 3, we characterize a system as a gathering of has that have indistinguishable bit designs in the system location segment of their locations. Albeit each of the 32 bits characterizes the Ipv4 host address, we have a variable number of bits that are known as the host bit of the location. The quantity of bits utilized as a part of this host share decides the quantity of has that we can have inside the system. Case in point, on the off chance that we have to have no less than 200 hosts in a specific system, we would need to utilize enough bits as a part of the host segment to have the capacity to speak to no less than 200 diverse bit designs. To allot an exceptional location to 200 hosts, we would utilize the whole last octet. With 8 bits, an aggregate of 256 diverse bit examples could be attained. This would imply that the bits for the upper three octets would speak to the system parcel.
Positional Notations
Figuring out how to change over double to decimal obliges an understanding of the numerical premise of a numbering framework called positional documentation. Positional documentation implies that a digit speaks to diverse qualities relying upon the position it involves. All the more particularly, the esteem that a digit speaks to is that esteem duplicated by the force of the base, or radix, spoke to by the position the digit involves. A few illustrations will help to illuminate how this framework functions. For the decimal number 245, the esteem that the 2 speaks to is 2*10^2 (2 times 10 to the force of 2). The 2 is in what we ordinarily allude to as the "100s" position. Positional documentation alludes to this position as the base^2 positions in light of the fact that the base, or radix, is 10 and the force are 2.
Networking Prefixes
An imperative inquiry is: How would we know what number of bits speaks to the system parcel and what number of bits speak to the host bit? When we express an Ipv4 system address, we add a prefix length to the system address. The prefix length is the quantity of bits in the address that provides for us the system share. For instance, in 172.16.4.0/24, the/24 is the prefix length - it lets us know that the initial 24 bits are the system address. This leaves the staying 8 bits, the last octet, as the host bit. Later in this section, we will take in more about an alternate element that is utilized to define the system bit of an Ipv4 location to the system gadgets. It is known as the subnet veil. The subnet veil comprises of 32 bits, pretty much as the location does, and utilizes 1s and 0s to demonstrate which bits of the location are system bits and which bits are host bits. Systems are not generally doled out a/24 prefix. Contingent upon the quantity of hosts on the system, the prefix relegated may be diverse. Having an alternate prefix number changes the host go and show address for each one system. Recognize that the system location could continue as before, however the host extent and the show location are diverse for the distinctive prefix lengths. In this figure you can likewise see that the quantity of has that could be tended to on the system changes too.
ARP
The ARP Cache (Neighbor Cache) can contain two fundamental sorts of passages; Permanent entrances (Static sections), and Dynamic passages. Dynamic passages will be demonstrated as Incomplete, Reachable, Stale, Delay or Probe. It is suggested that you utilize Dynamic entrances as default; however there are a few occurrences where a Static section is exhorted. A case would be when decommissioning a server and supplanting it with an alternate server imparting the old DNS Name and IP Address. In this case, you may think about utilizing as an impermanent static mapping for the new server in your Router ARP Tables. At that point erase the old ARP Cache on your servers. The issue is that the switch's substitute ARP solicitations give back where it's due MAC location to the sending host. Thus, the sending host sends its activity to the wrong MAC address. As it were, the issue originates from substitute ARP answers.
To address this issue, utilization Network Monitor utilizes a catch a follow. On the off chance that the follow uncovers that when a sending host sends an ARP demand for the MAC location of an objective IP address, a gadget (normally a switch) answers with a MAC address other than the goal's right MAC address. To figure out whether this is the issue, check the ARP store of the source host to verify it is getting the right IP location to MAC address determination. On the other hand, you can catch all activity with Network Monitor and later channel the caught movement to show just the ARP and RARP conventions. The RARP convention changes over MAC locations to IP addresses and is characterized in RFC 903. You can settle the ARP issue by debilitating 'Substitute ARP' on the culpable gadget. Precisely how this is carried out relies on upon the gadget's make and model; counsel the producer's documentation.
DHCP relay and server
The DHCP convention supplies programmed arrangement parameters, for example, an IP address with a subnet veil, default portal, DNS server location, and Wireless Integrated Network Sensor (WINS) location to has. At first, DHCP customers have none of these arrangement parameters. With a specific end goal to acquire this data, they send a telecast demand for it. At the point when a DHCP server sees this ask for, the DHCP server supplies the fundamental data. Because of the way of these show asks for, the DHCP customer and server must be on the same subnet. Layer 3 gadgets, for example, switches and firewalls don't ordinarily forward these show asks for as a matter of course.
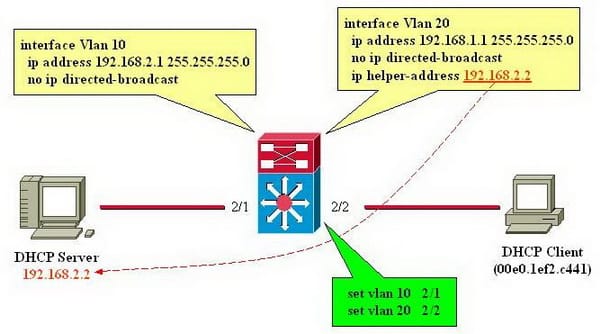
Check that the interface on the Windows 2000 Router that associates with the system where the DHCP customers are spotted is added to the DHCP Relay Agent IP steering convention. Check that the Relay DHCP parcels check box is chosen for the DHCP Relay Agent interface associated with the system where the DHCP customers are placed. Check that the IP locations of DHCP servers designed on the worldwide properties of the DHCP Relay Agent are the right IP addresses for DHCP servers on your internetwork.
DHCP protocol operations
From the switch with the DHCP Relay Agent empowered, utilize the PING utility to ping each of the DHCP servers arranged in the worldwide DHCP Relay Agent dialog. In the event that you can't ping the DHCP servers from the DHCP Relay Agent switch, troubleshoot the absence of integration between the DHCP Relay Agent switch and the DHCP server or servers. Confirm that IP bundle separating is not keeping the accepting (through info channels) or sending (through yield channels) of DHCP movement. DHCP movement utilizes the UDP ports of 67 and 68. Confirm that TCP/IP sifting on the switch interfaces is not keeping the getting of DHCP activity.
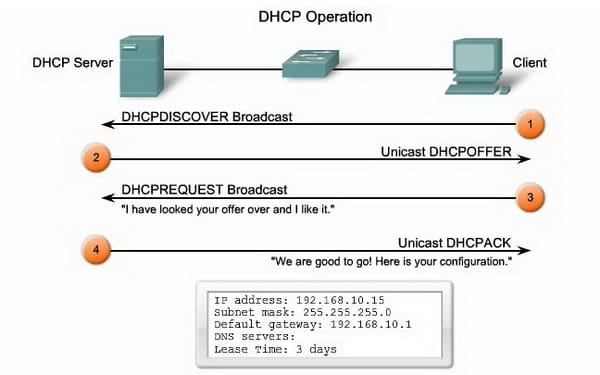
An endeavor to place DHCP customers and a DHCP server on the same subnet may not generally be advantageous. In such a circumstance, you can utilize DHCP hand-off. At the point when the DHCP hand-off executor on the security apparatus gets a DHCP demand from a host on an inside interface, it advances the appeal to one of the determined DHCP servers on an outside interface. At the point when the DHCP server answers to the customer, the security apparatus advances that answers back. Therefore, the DHCP transfer executor goes about as a substitute for the DHCP customer in its discussion with the DHCP server. System activity now and again falls flat on the grounds that a switch's substitute ARP solicitation furnishes a proportional payback address. A switch makes this ARP ask for an IP address on its internal subnets (pretty much as a remote access server makes a solicitation on the LAN for its remote access customers).
Site Search:






