- Home
- Popular IT Certifications
- How to Install and Configure Routers and Switches
How to install and configure routers and switches
Installation and configuration of network devices is one of the most important tasks which ensure the smooth running of the system. If you are properly able to configure and install you devices, then you will save yourself from loads from problems which might occur to you in the future. A network functions perfectly when all the switches and routers are connected to all the other devices on the network, through wired or wireless connections. The correct configuration of these devices ensures that there will be a healthy flow of data traffic and no problem will be caused. In this regard, there is always an extra focus on the process of configuration and installation of routers and switches and all the related devices. In fact, there are various other elements, procedures and methods which are involved in this process. Although you may try to manage the process on your own using your own judgment, but it will be much preferred and will be easier for you as well if you stick to the basic methods which have been described to go about this process. If you master these processes, you will surely perform the process of installation and configuration with perfection.
Routing Tables
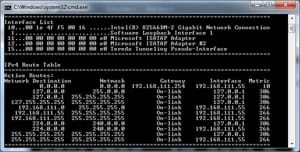
Routing tables are one of the most important entities which help in the determination of the path from data packages. Routing tables comprise of all the information regarding the location of each router and its distance from each other. In fact, it contains the whole topology of the network and knows each and every route. Routing tables are generally stored in routers. Whenever a data package arrives at a router, it consults the routing tables to figure the smallest and most probable path for data to travel. The data is then directed to this route to make sure that it reaches the destination in the least amount of time. The information regarding the network structure is manually stored on routing tables, and each of the routers has got a copy of it. The existence of routing tables is extremely important to make sure that there is an effective flow of data traffic and there is no congestion on any route.
NAT
NAT is also referred to as Network Address Translation. Since we are aware of the fact that there are many forms of IP Addresses which are used in different situations, it is essential to have a service that could translate one form of IP Address to another form of IP Address. This is what the NAT service does for you. It ensures effective transmission of data over the networks by translation IP Addresses into different forms. One example can be when data is sent from a private network over the internet; in this case it is essential to translate the IP Addresses to enable both networks to work on common grounds. NAT service is generally configured on computers or routers. The device configured with NAT service comprises of tables which consist of one-to-one mapping of IP Addresses of one format on the IP Addresses of the other format. In this way, it is ensured that the routers know the IP Addresses of the destination devices in the correct format.
PAT
PAT is the abbreviation of Port Address Translation. Nowadays, it is common for many devices inside the same network to have the same external address, from example the address of the router they are connected to, it becomes difficult to discriminate between the devices. In this regard, the Port Address Translation service has been developed. The main purpose of this service is to assign different port numbers to the devices in on network. This will ensure that the data packets get to their exact destination. PAT is generally configured on routers, but can also work on other devices as well. Whenever a data packet passes through the device using PAT, the destination address on the data packet is changed and it is assigned a particular port number. In this way, the data packets will reach the exact port where their destination is. This is possible because the PAT device consists of a table where it stores the actual address of each computer in correspondence to its assigned port number.
VLAN (trunking)
VLAN is also known as "Virtual Local Area Network". The basic purpose of a VLAN is to make sure that there is no physical restriction on the connection of layer 2 switches. These networks hold the ability to span different switches without having any physical restriction. It also adds an extra layer of security by separating the physical networks from the logical ones. In this process, these networks make use of special links between these switches to carry the VLAN. These special links are referred to as Trunks and the process is known as Trunking. VLAN trunking offers a cheap and reliable way to manage load of virtual network connections.
Managed vs. Unmanaged
There are basically two types of devices in a network, depending on the complexity and size of the network. The devices might me managed or they may be unmanaged.
Unmanaged Devices are those devices which do not require any special configuration on part of the user. These devices are basically used in networks which are extremely simple and small. Under these conditions, the devices such as routers or switches are able to configure themselves on their own. These devices are referred to as unmanaged devices. However, this means that users generally do not have much control over the unmanaged devices.
Managed Devices are those devices in which the settings are configured manually by the users. These are used for networks which are complex are quite large. There provide great control over the LAN traffic and also allow the users to control many other features. This means that you are able to configure and make a lot of changes on managed devices according to your convenience. In addition to this, the access to these devices can also be restricted which proves to be more secure.
Interface Configurations
Full Duplex: A Duplex is generally a direct communication between two devices. Full Duplex is a two-way communication process in which you can send and receive messages at the same time. This simultaneous sending and receiving of messages allow the conversation to be interactive. Full Duplex is a widely used method for communication. You can relate to it using the example of a telephone, where two-way traffic is flowing during the conversation.
Half Duplex: Half Duplex is quite different from a Full Duplex in the way that messages can be either sent or received in this communication. This means that, while you are sending a message you cannot receive it until your message has been sent. This is not an effective form of communication and is not used in the modern day.
Port Speeds: It is not untrue that different switches in a network are able to work at varying speeds. This is because most of them are designed to cater to a particular speed during the communication. In this regard, it is essential to make sure that the port speeds on both devices which are communicating are synchronized. These speeds can be set to synchronize automatically or they can be set manually.
IP Addressing: The most common type of IP Addresses is IPv4 addresses, which are made up of 32 bits. It is quite essential for each device on a network to have a separate IP Address. In this regard, the IP addresses can be assigned to the systems manually as well as automatically. The automatic assigning of IP Addresses is done by DHCP servers. Each device must have a different IP Address to make sure that data packages can be sent to their exact destinations.
MAC Filtering: You are aware of the fact that MAC Address is the physical address which is assigned separately to the NIC of system on the network. MAC addresses usually work with switches in the layer 2. The concept of MAC filtering allows you to configure your switches in a way that only data packets associated with certain MAC address are able to pass through the switch. This will increase the security of your network and will also provide you will better control.
PoE

PoE is also known as "Power over Ethernet". The basic concept behind PoE is to enable the transmission of electric power over an Ethernet cable. This concept is basically used to transmit data to routers or other devices which are quite far away. The data is transferred in the cable along with the current. Many of the switches, routers and computers use the concept of PoE to operate from remote locations effectively. PoE allows all of these remote devices to be powered from one source of power which is usually centralized.
Traffic Filtering
Traffic filtering in networking refers to the filtering of traffic in a network, which enables some traffic to flow while stops the remaining traffic. This is quite essential to make sure that only the required amount of traffic flows through the network. This can also add a layer of security because it will control which data, protocols etc. you allow to pass through your network. Traffic filtering can be of various kinds depending on the type of network you are using and your requirement as well. For example, you can filter any protocols which you feel will not aid you in your process.
Diagnostics
This is the process in which you actually monitor the performance of your whole network to make sure that it is working perfectly. Yes, this means that once you have configured and installed all the devices, you need to diagnose the system to ensure that they are working properly. In this regard, you need to define a system which will enable you to access all the required information which will be helpful to you. You will make use of this information to check whether everything is working fine or there is still any room for improvement. It is a very integral process in this regard.
VTP Configuration
VTP is referred to as VLAN Trunking Protocol. This protocol allows you the facility to configure your VLAN settings on one switch which can be learned by all other client switches in the network. This switch performs the role of a server and is fed with all the required information. VTP allows this information and settings to be inherited by all other switches on the network. This saves you from a good amount of effort which you had to do otherwise. Any changes to this main server switch will make changes to all the switches in the network.
QoS
QoS is the abbreviation of Quality of Service. In a complex and large network, traffic is flowing from different directions and from different points. Quality of Service is the technique which allows you to divide this traffic and set priorities for them based on their importance. This will enable you to decide that which traffic is important for you and should be given the high preference and the highest amount of bandwidth. In fact, this service will enable you to make use of your bandwidth in the best possible way.
Port Mirroring
Port Mirroring is the process in which a copy of data packets is made and stored for the process of monitoring the processes. The traffic flowing through the network cannot be disrupted for the process of monitoring as this may cause complications. This is the reason why port mirroring is used to monitor the traffic and store it to ensure that everything is going perfect. In fact, port mirroring is a very important process that ensures that there is no disruption in the system of the network.
All of elements which we discussed above are of high significance. It is quite essential to install and configure the devices in the best possible way in order to avoid future complications. There are many techniques developed which ensure that these processes are carried out effectively and you do not encounter any problem. If one is able to understand all of these concepts clearly, one will surely be able to master the installation and configuration of switches and routers.
Site Search:






